Read an article http://www.information-age.com/email/channels/security-and-continuity/perspectives-and-trends/2105738/can-satellites-be-hacked.thtml which discuss the report that hackers believed to be operating from China, had managed in 2008 to interfere with two
US government satellites. The hackers reportedly took control of the Landsat-7 and Terra AM-1 satellites for a grand total of 12 minutes and two minutes respectively, the report claimed.
The article goes onto say it is doubted whether hackers would have had the wherewithal to send tracking and
telemetry data up to the Skynet satellite. This is implying that the hackers would of used there own infrastructure to do the hack, which I think is misleading, why build your own infrastructure when NASA and other organisations already have the infrastructure in place. What is there to prevent hackers from controlling a satellite via a compromised system in one of the many military or space agencies systems around the world with the capability to communicate with satellites.
Although Gary McKinnon who is one of many that have been accused of hacking NASA systems, NASA have always denied anyone has had access to critical resources. Would NASA admit a breach, has one gone undetected, could one occur in the future.
Thursday 31 May 2012
Cookies: 3rd party, tracking and contextual marketing
Cookies have some important implications for Web users. While cookies
are sent only to the server setting them or the server in the same Internet
domain, a Web page may contain images or other components stored on servers in
other domains. Cookies that are set during retrieval of these components are
called third-party cookies. The standards for cookies, RFC 2109 and RFC 2965,
specify that browsers should protect user privacy and not allow third-party
cookies by default. But most browsers do allow third-party cookies by default.
These cookies may be used to track internet users' web browsing habits.
This can also be done in part by using the IP address of the computer
requesting the page or the referrer field of the HTTP request header, but
cookies allow for greater precision.
If the user requests a page of the site, but the request contains no
cookie, the server presumes that this is the first page visited by the user;
the server creates a random string and sends it as a cookie back to the browser
together with the requested page;
From this point on, the cookie will be automatically sent by the browser
to the server every time a new page from the site is requested; the server
sends the page as usual, but also stores the URL of the requested page, the
date/time of the request, and the cookie in a log file.
By analyzing the log file collected in the process, it is then possible
to find out which pages the user has visited, and in what sequence.
Marketing companies can use cookies through affiliate programs to send
adverts to web browsers that are dependent on the users browsing history as
recorded by the marketing company’s database.
Tuesday 29 May 2012
Why we have information security?
We implement information security to protect the
confidentiality, integrity and availability of our resources, but what is the
real reason for implementing? It is very difficult to stop the determined individual
of group of individuals from attack our cyber infrastructure.
If we lived in a utopian world then we would not need information security as no one would abuse the systems, however they are very few people are totally honest, and there a lot of the population who could be tempted if the motivation was sufficient to ‘bend’ the rules.
We tend to think that people are either honest or dishonest, a binary assessment for the digital age. Society likes to believe that most people are honest, but a few bad apples spoil the bunch. If this were true, it would be easily remedy some of society’s problems with cheating and dishonesty. Human-resources departments could screen for cheaters when hiring. Dishonest financial advisers or building contractors could be flagged quickly and shunned. Cheaters in sports and other arenas would be easy to spot before they rose to the tops of their professions.
However it is not as straight forward as people being honest or dishonest, there are multiple levels between a total honest individual and a total dishonest one.
“Another 1% will always be dishonest and always try to pick your lock and steal your television; locks won't do much to protect you from the hardened thieves, who can get into your house if they really want to. The purpose of locks, the locksmith said, is to protect you from the 98% of mostly honest people who might be tempted to try your door if it had no lock.”
http://online.wsj.com/article/SB10001424052702304840904577422090013997320.html?mod=wsj_share_tweet
If we lived in a utopian world then we would not need information security as no one would abuse the systems, however they are very few people are totally honest, and there a lot of the population who could be tempted if the motivation was sufficient to ‘bend’ the rules.
We tend to think that people are either honest or dishonest, a binary assessment for the digital age. Society likes to believe that most people are honest, but a few bad apples spoil the bunch. If this were true, it would be easily remedy some of society’s problems with cheating and dishonesty. Human-resources departments could screen for cheaters when hiring. Dishonest financial advisers or building contractors could be flagged quickly and shunned. Cheaters in sports and other arenas would be easy to spot before they rose to the tops of their professions.
However it is not as straight forward as people being honest or dishonest, there are multiple levels between a total honest individual and a total dishonest one.
The article “Why we lie” in the Wall Street Journal has a
great statement about why locks are fitted to our doors, and this statement
fits well with our cyber security.
“Another 1% will always be dishonest and always try to pick your lock and steal your television; locks won't do much to protect you from the hardened thieves, who can get into your house if they really want to. The purpose of locks, the locksmith said, is to protect you from the 98% of mostly honest people who might be tempted to try your door if it had no lock.”
http://online.wsj.com/article/SB10001424052702304840904577422090013997320.html?mod=wsj_share_tweet
Hardware Backdoors
For a while now there have been stories circulating the Internet about hardware produced in countries such as China have backdoors built in to them and the equipment is being used in Government and Military infrastructure.
There have been a number of articles related to the original from well established security bloggers.
http://erratasec.blogspot.fr/2012/05/bogus-story-no-chinese-backdoor-in.html
http://securityaffairs.co/wordpress/5889/security/china-made-us-military-chip-security-backdoor-or-debugging-functionality.html
Which question as whether it is a deliberate backdoor or debugging tool, read the articles and judge for yourself.
One of my first reactions on reading the original story was to google the researcher name to see if he was actually a researcher a Cambridge, and he does seem to be a legitimate researcher.
As to whether it is a deliberate backdoor or not, I'm not sure, however there are some good questions and points raised.
It does show that hardware and software are slowly merging with programmable chips becoming part of mainstream production rather rapid prototyping. The whole affair did remind me of a conversation I had with a colleague in the mid 80's about using a reprogramme ROM and programmable logic gates to build a computer that could redesign and reprogramme itself.
If we look at the history of backdoors, one of the earliest cases of implementing a backdoor during production was described by Ken Thompson who along with Dennis Ritchie, received the ACM Turing award in 1983, for "for their development of generic operating systems theory and specifically for the implementation of the UNIX operating system.". In his Turing award lecture, Reflections On Trusting Trust, Ken Thompson described a hack that he placed into early UNIX systems: the C compiler would insert a back door whenever it compiled the login program, allowing Ken Thompson to access any UNIX system. The scheme was so fiendish that if you tried remove the back-door generating code from the source code and recompile the compiler, the compiler would reintroduce the back door generation into the source code!
This demonstrated that it was possible to introduce a backdoor into an application even through the source code had no backdoor, through out history there have been rumours of all sorts of industrial espionage being conducted and the military are often accursed of implementing hidden functionality into all sorts of equipment, so it is no surprise that the Chinese are being accused of do so, and Huawei (Officially Huawei Technologies Co. Ltd.) is a Chinese multinational networking and telecommunications equipment and services company. It is the second-largest supplier of mobile telecommunications infrastructure equipment in the world (after Ericsson). Is often linked to such activities. Earlier this year Australia blocked Huawei from tendering for contracts in the country's
$38 billion National Broadband Network (NBN) due to cyber security concerns. Huawei is one of the vendors for BT 21st Century Network in the UK.
In the last couple of weeks there has been stories circulating about a backdoor discovered in a chip manufactured in China for the Military.
http://www.cl.cam.ac.uk/~sps32/sec_news.html#Assurance
" We chose an American military chip that is highly secure with sophisticated encryption standard, manufactured in China. Our aim was to perform advanced code breaking and to see if there were any unexpected features on the chip. We scanned the silicon chip in an affordable time and found a previously unknown backdoor inserted by the manufacturer. This backdoor has a key, which we were able to extract. If you use this key you can disable the chip or reprogram it at will, even if locked by the user with their own key. This particular chip is prevalent in many systems from weapons, nuclear power plants to public transport. "
There have been a number of articles related to the original from well established security bloggers.
http://erratasec.blogspot.fr/2012/05/bogus-story-no-chinese-backdoor-in.html
http://securityaffairs.co/wordpress/5889/security/china-made-us-military-chip-security-backdoor-or-debugging-functionality.html
Which question as whether it is a deliberate backdoor or debugging tool, read the articles and judge for yourself.
One of my first reactions on reading the original story was to google the researcher name to see if he was actually a researcher a Cambridge, and he does seem to be a legitimate researcher.
As to whether it is a deliberate backdoor or not, I'm not sure, however there are some good questions and points raised.
- Are countries / industry building backdoors in - very likely and not just the Chinese.
- Is the technique identified by the researcher valid and useful - yes.
- Was it a hidden backdoor - need more information on the findings
It does show that hardware and software are slowly merging with programmable chips becoming part of mainstream production rather rapid prototyping. The whole affair did remind me of a conversation I had with a colleague in the mid 80's about using a reprogramme ROM and programmable logic gates to build a computer that could redesign and reprogramme itself.
Monday 28 May 2012
Tools (28th May)
Weekly round up of pen test and forensic tools that have come to my attention over the last week, it is not a comprehensive tool list but tools that I found interesting or details of tools I use that have been upgrade.
Security analysis tool Trisul 2.4 released
http://trisul.org/
is a kind of network monitor that supplements fine grained traffic metering with flows, packets, and alerts. You can carry out any kind of network and security analysis.
Nmap 6 released
http://nmap.org/
Nmap is a free and open source utility for network exploration or security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
Saint 7.13
http://www.saintcorporation.com/
SAINT releases new product version 7.13 including support for Ubuntu 12.04 LTS; content search enhancemnts; expanded diagnostics for blind SQL injection; CVSS scoring in all default reports; and lots more.
CSRF-Request-Builder
https://github.com/TheRook/CSRF-Request-Builder
This is a tool for testing CSRF against web services. This is a complete test in that it can be used to create PoC exploits to exploit real victims and real systems in a real world scenario. After all if it didn't work in the real world it wouldn't be a useful test
The Social-Engineer Toolkit (SET) 3.3 Codename “DerbyCon 2.0 Edition” has been released.
https://www.secmaniac.com/blog/2012/05/21/the-social-engineer-toolkit-set-3-3-codename-derbycon-2-0-edition-has-been-released/
“The Social Engineering Toolkit (SET) is an open source, python-driven, social-engineering penetration testing framework of custom tools which solely focuses on attacking the human element of penetration testing.
Security analysis tool Trisul 2.4 released
http://trisul.org/
is a kind of network monitor that supplements fine grained traffic metering with flows, packets, and alerts. You can carry out any kind of network and security analysis.
Nmap 6 released
http://nmap.org/
Nmap is a free and open source utility for network exploration or security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
Saint 7.13
http://www.saintcorporation.com/
SAINT releases new product version 7.13 including support for Ubuntu 12.04 LTS; content search enhancemnts; expanded diagnostics for blind SQL injection; CVSS scoring in all default reports; and lots more.
CSRF-Request-Builder
https://github.com/TheRook/CSRF-Request-Builder
This is a tool for testing CSRF against web services. This is a complete test in that it can be used to create PoC exploits to exploit real victims and real systems in a real world scenario. After all if it didn't work in the real world it wouldn't be a useful test
The Social-Engineer Toolkit (SET) 3.3 Codename “DerbyCon 2.0 Edition” has been released.
https://www.secmaniac.com/blog/2012/05/21/the-social-engineer-toolkit-set-3-3-codename-derbycon-2-0-edition-has-been-released/
“The Social Engineering Toolkit (SET) is an open source, python-driven, social-engineering penetration testing framework of custom tools which solely focuses on attacking the human element of penetration testing.
Sunday 27 May 2012
implied consent (cookies)
Just been reading the http://www.guardian.co.uk/technology/2012/may/26/cookies-law-changed-implied-consent about the latest information about cookies from the ISO. In the article it says "In an updated version of its advice for websites on how to use cookies – small text files that are stored on the user's computer and can identify them – the Information Commissioner's Office (ICO) has said that websites can assume that users have consented to their use of them." This is not true the advice from the Information Commissioner’s guidance made it clear that although an explicit opt-in mechanism might provide regulatory certainty it was not the only means of gaining consent.
The latest version v3 of the adice from the ICO says the following
To explain further it might be useful to unpack what we actually mean by the term "implied consent" remembering throughout that consent (whether it is implied or express) has to be a freely given, specific and informed indication of the individual’s wishes. For implied consent to work there has to be some action taken by the consenting individual from which their consent can be inferred. This might for example be visiting a website, moving from one page to another or clicking on a particular button. The key point, however, is that when taking this action the individual has to have a reasonable understanding that by doing so they are agreeing to cookies being set.
The still requires the user to be informed and some form of interaction is required, at the basic level a note saying that "using this site implies permission for us to use cookies" should be given with info on the cookie usage available.
The latest version v3 of the adice from the ICO says the following
Implied consent is certainly a valid form of consent but those who seek to rely on it should not see it as an easy way out or use the term as a euphemism for "doing nothing". In many cases, to create a situation in which implied consent is acceptable to subscribers, users and the regulator it would still be necessary to follow the steps set out in the Information Commissioner’s existing guidance.
To explain further it might be useful to unpack what we actually mean by the term "implied consent" remembering throughout that consent (whether it is implied or express) has to be a freely given, specific and informed indication of the individual’s wishes. For implied consent to work there has to be some action taken by the consenting individual from which their consent can be inferred. This might for example be visiting a website, moving from one page to another or clicking on a particular button. The key point, however, is that when taking this action the individual has to have a reasonable understanding that by doing so they are agreeing to cookies being set.
The still requires the user to be informed and some form of interaction is required, at the basic level a note saying that "using this site implies permission for us to use cookies" should be given with info on the cookie usage available.
Monday 21 May 2012
Prudent man rule
From the financial world based on a case “Harvard College v. Amory” in a 1830 Massachusetts court. The prudent man rule directs trustees "to observe how men of prudence, discretion and intelligence manage their own affairs, not in regard to speculation, but in regard to the permanent disposition of their funds, considering the probable income, as well as the probable safety of the capital to be invested." In summary it meant that people in charge of other people's money must exercise due care and skill, and look after the money as if it were their own.
"prudent man" would invest his own property with the following factors in mind:
the needs of beneficiaries;
the need to preserve the estate (or corpus of the trust);
the amount and regularity of income
The terms reasonable and prudent person, due care and due diligence have been used in the fields of Finance, Securities, and Law for many years. In recent years these terms have found their way into the fields of computing and information security.
Shon Harris offers the following definitions of due care and due diligence:
"Due care are steps that are taken to show that a company has taken responsibility for the activities that take place within the corporation and has taken the necessary steps to help protect the company, its resources, and employees." And, [Due diligence are the] "continual activities that make sure the protection mechanisms are continually maintained and operational."
Under legislation senior corporate officers can be personally subject to up to millions in fines or possible if their organisations do not comply with the law.
Management is obligated to protect the business from losses due to natural disasters, malicious code, compromise of proprietary information, and damage to reputation, violation of the law, employee privacy suits, and stockholder suits. Management must follow the "prudent man rule" that requires officers to perform duties with diligence and care that ordinary, prudent people would exercise under similar circumstances. The officers must exercise "due care" or "reasonable care" to carry out their responsibilities to the organization. In exercising due care, corporate officers must institute protections for areas such as access to resources and data confidentiality.
From a legal point of view, there are a few basic rules which will determine if a company being sued is liable or not. One of the basic rules is “the prudent man rule”, in which the court will try to determine whether the company or individual was acting as a responsible entity. For example, if a database was hacked and a client’s personal data was stolen, the court will attempt to understand if and how the company tried to protect its clients’ data in a prudent and responsible way. Another way for the court to determine liability is by checking if the company exercised due diligence and care. If we go back to the previous example, the court will try to uncover if the company exercised due diligence and researched the potential risks related to the database information, and what actions it took to protect it.
In criminal law, due diligence (also known as due care) is the only available defence to a crime that is one of strict liability (i.e., a crime that only requires an actus reus and no mens rea). Once the criminal offence is proven, the defendant must prove on balance that they did everything possible to prevent the act from happening. It is not enough that they took the normal standard of care in their industry - they must show that they took every reasonable precaution.
Information security due diligence is often undertaken during the information technology procurement process to ensure risks are known and managed. Companies need to practice due care in the operation of their IT systems to prevent security breaches and to have controls in place to mitigate the effect when breaches occur. Failure to practice such due diligence is negligence and increases business risk.
"prudent man" would invest his own property with the following factors in mind:
The terms reasonable and prudent person, due care and due diligence have been used in the fields of Finance, Securities, and Law for many years. In recent years these terms have found their way into the fields of computing and information security.
Shon Harris offers the following definitions of due care and due diligence:
"Due care are steps that are taken to show that a company has taken responsibility for the activities that take place within the corporation and has taken the necessary steps to help protect the company, its resources, and employees." And, [Due diligence are the] "continual activities that make sure the protection mechanisms are continually maintained and operational."
Under legislation senior corporate officers can be personally subject to up to millions in fines or possible if their organisations do not comply with the law.
Management is obligated to protect the business from losses due to natural disasters, malicious code, compromise of proprietary information, and damage to reputation, violation of the law, employee privacy suits, and stockholder suits. Management must follow the "prudent man rule" that requires officers to perform duties with diligence and care that ordinary, prudent people would exercise under similar circumstances. The officers must exercise "due care" or "reasonable care" to carry out their responsibilities to the organization. In exercising due care, corporate officers must institute protections for areas such as access to resources and data confidentiality.
From a legal point of view, there are a few basic rules which will determine if a company being sued is liable or not. One of the basic rules is “the prudent man rule”, in which the court will try to determine whether the company or individual was acting as a responsible entity. For example, if a database was hacked and a client’s personal data was stolen, the court will attempt to understand if and how the company tried to protect its clients’ data in a prudent and responsible way. Another way for the court to determine liability is by checking if the company exercised due diligence and care. If we go back to the previous example, the court will try to uncover if the company exercised due diligence and researched the potential risks related to the database information, and what actions it took to protect it.
In criminal law, due diligence (also known as due care) is the only available defence to a crime that is one of strict liability (i.e., a crime that only requires an actus reus and no mens rea). Once the criminal offence is proven, the defendant must prove on balance that they did everything possible to prevent the act from happening. It is not enough that they took the normal standard of care in their industry - they must show that they took every reasonable precaution.
Information security due diligence is often undertaken during the information technology procurement process to ensure risks are known and managed. Companies need to practice due care in the operation of their IT systems to prevent security breaches and to have controls in place to mitigate the effect when breaches occur. Failure to practice such due diligence is negligence and increases business risk.
CISSP, CISA & CISM (Frameworks)
These three certifications are vendor neutral, however there all refer to a range of frameworks throughout their individual domains. In each case it is not necessary to be fully conversant with the fine detail of each domain but there are some frameworks that are more pre-dominate than others.
COBIT
COBIT is a framework created by ISACA for information technology (IT) management and IT Governance. It is a supporting toolset that allows managers to bridge the gap between control requirements, technical issues and business risks.
http://en.wikipedia.org/wiki/COBIT
The COBIT components include:
Published standards
SABSA
SABSA is a model and a methodology for developing risk-driven enterprise information security architectures and for delivering security infrastructure solutions that support critical business initiatives.
http://en.wikipedia.org/wiki/Sherwood_Applied_Business_Security_Architecture
The SABSA Matrix applies the what (Assets), why (motivation), how (process), who (people), where (location), and when (time) to the 6 layers contextual, conceptual, logical, physical, component, and operational.
TOGAF
The Open Group Architecture Framework (TOGAF®) is a framework for enterprise architecture which provides a comprehensive approach for designing, planning, implementation, and governance of enterprise information architecture.
http://en.wikipedia.org/wiki/The_Open_Group_Architecture_Framework
An architecture framework is a set of tools which can be used for developing a broad range of different architectures. It should:
COBIT
COBIT is a framework created by ISACA for information technology (IT) management and IT Governance. It is a supporting toolset that allows managers to bridge the gap between control requirements, technical issues and business risks.
http://en.wikipedia.org/wiki/COBIT
The COBIT components include:
- Framework: Organize IT governance objectives and good practices by IT domains and processes, and links them to business requirements
- Process descriptions: A reference process model and common language for everyone in an organization. The processes map to responsibility areas of plan, build, run and monitor.
- Control objectives: Provide a complete set of high-level requirements to be considered by management for effective control of each IT process.
- Management guidelines: Help assign responsibility, agree on objectives, measure performance, and illustrate interrelationship with other processes
- Maturity models: Assess maturity and capability per process and helps to address gaps.
ISO/IEC27000
The ISO/IEC 27000-series (also known as the 'ISMS Family of Standards' or 'ISO27k' for short) comprises information security standards published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
http://en.wikipedia.org/wiki/ISO/IEC_27000-series Published standards
- ISO/IEC 27000 — Information security management systems — Overview and vocabulary [1]
- ISO/IEC 27001 — Information security management systems — Requirements
- ISO/IEC 27002 — Code of practice for information security management
- ISO/IEC 27003 — Information security management system implementation guidance
- ISO/IEC 27004 — Information security management — Measurement
- ISO/IEC 27005 — Information security risk management
- ISO/IEC 27006 — Requirements for bodies providing audit and certification of information security management systems
SABSA
SABSA is a model and a methodology for developing risk-driven enterprise information security architectures and for delivering security infrastructure solutions that support critical business initiatives.
http://en.wikipedia.org/wiki/Sherwood_Applied_Business_Security_Architecture
The SABSA Matrix applies the what (Assets), why (motivation), how (process), who (people), where (location), and when (time) to the 6 layers contextual, conceptual, logical, physical, component, and operational.
The Open Group Architecture Framework (TOGAF®) is a framework for enterprise architecture which provides a comprehensive approach for designing, planning, implementation, and governance of enterprise information architecture.
http://en.wikipedia.org/wiki/The_Open_Group_Architecture_Framework
An architecture framework is a set of tools which can be used for developing a broad range of different architectures. It should:
- describe a method for defining an information system in terms of a set of building blocks
- show how the building blocks fit together
- contain a set of tools
- provide a common vocabulary
- include a list of recommended standards
- include a list of compliant products that can be used to implement the building blocks
Tools (21st May)
Weekly round up of pen test and forensic tools that have come to my attention over the last week, it is not a comprehensive tool list but tools that I found interesting or details of tools I use that have been upgrade.
Common Vulnerability Reporting Framework updated
http://www.icasi.org/cvrf
The Industry Consortium for Advancement of Security on the Internet (ICASI) announced Common Vulnerability Reporting Framework (CVRF), Version 1.1. Enhancements offer users a more comprehensive and flexible format, while reducing duplication and the possibility of errors.
L0phtCrack 6.0.15
http://www.l0phtcrack.com/
L0phtCrack 6 is packed with powerful features such as scheduling, hash extraction from 64 bit Windows versions, multiprocessor algorithms, and networks monitoring and decoding.
Wifite v2 Alpha
http://code.google.com/p/wifite/
to test multiple WEP and WPA encrypted networks at the same time. this tool is customizable to be automated with only a few arguments. wifite can be trusted to run without supervision.
SkunxTools
http://sourceforge.net/projects/skunxtools/
In its current phase it currently scans google dorks and tests for sql vulnerabilities. Once urls are harvested from google dorks they are saved to a log file for future reference. One a sql check is run, the vulnerable URLs are saved to a seperate log file
Update ESSPEE x32 - Penetration Testing & Forensics
http://sourceforge.net/projects/esspee/
ESSPEE is a derivetive of Back | Track 5, based on Ubuntu 12.04. Designed for users who wish to use only free software. It is packed with featured security tools with stable configurations. This version consolidates the Unity desktop interface; a brand new way to find and manage your applications.
Common Vulnerability Reporting Framework updated
http://www.icasi.org/cvrf
The Industry Consortium for Advancement of Security on the Internet (ICASI) announced Common Vulnerability Reporting Framework (CVRF), Version 1.1. Enhancements offer users a more comprehensive and flexible format, while reducing duplication and the possibility of errors.
L0phtCrack 6.0.15
http://www.l0phtcrack.com/
L0phtCrack 6 is packed with powerful features such as scheduling, hash extraction from 64 bit Windows versions, multiprocessor algorithms, and networks monitoring and decoding.
Wifite v2 Alpha
http://code.google.com/p/wifite/
to test multiple WEP and WPA encrypted networks at the same time. this tool is customizable to be automated with only a few arguments. wifite can be trusted to run without supervision.
SkunxTools
http://sourceforge.net/projects/skunxtools/
In its current phase it currently scans google dorks and tests for sql vulnerabilities. Once urls are harvested from google dorks they are saved to a log file for future reference. One a sql check is run, the vulnerable URLs are saved to a seperate log file
Update ESSPEE x32 - Penetration Testing & Forensics
http://sourceforge.net/projects/esspee/
ESSPEE is a derivetive of Back | Track 5, based on Ubuntu 12.04. Designed for users who wish to use only free software. It is packed with featured security tools with stable configurations. This version consolidates the Unity desktop interface; a brand new way to find and manage your applications.
Thursday 17 May 2012
Cookies (again)
Returning to an area I have previously done a number of blogs on which is Cookies and the Privacy and Electronic Communications Regulations (PECR) which although it came into force on May 25th 2011, the enforcement was postponed for 1 year and the Information Commissioners Office (ICO) will start to enforce it from the 25th of this month. Any website found guilty of using technologies to track a user's browsing behaviour without their consent or sending unwanted marketing emails to consumers could face a fine of up to £500,000.
The law involves a proactive approach to cookies with sites having to ask for permission for cookies to be used before any cookie is sent to the browser. The ICO's own site has a consent mechanism in place which has affected the site see the article "Cookie acceptances plummet when ICO requests permission, figures show" http://www.out-law.com/page-12042 on the out-law website.
An article on the BBC today "Cookies: Majority of government sites to miss deadline" http://www.bbc.co.uk/news/technology-18090118 shows that even through the government is responsible for passing and implementing the law which is based on an EU directive Directive 2002/58 on Privacy and Electronic Communications and the amendment's introduced by Directive 2009/136 which means that the requirements have been know about for 3 years, the government own sites are going to fail to meet the deadline this month despite the 1 year period of grace given between the law coming in to force and actually been enforced.
The law involves a proactive approach to cookies with sites having to ask for permission for cookies to be used before any cookie is sent to the browser. The ICO's own site has a consent mechanism in place which has affected the site see the article "Cookie acceptances plummet when ICO requests permission, figures show" http://www.out-law.com/page-12042 on the out-law website.
An article on the BBC today "Cookies: Majority of government sites to miss deadline" http://www.bbc.co.uk/news/technology-18090118 shows that even through the government is responsible for passing and implementing the law which is based on an EU directive Directive 2002/58 on Privacy and Electronic Communications and the amendment's introduced by Directive 2009/136 which means that the requirements have been know about for 3 years, the government own sites are going to fail to meet the deadline this month despite the 1 year period of grace given between the law coming in to force and actually been enforced.
Monday 14 May 2012
Tools (14th May)
Weekly round up of pen test and forensic tools that have come to my attention over the last week, it is not a comprehensive tool list but tools that I found interesting or details of tools I use that have been upgrade.
New Version Of CORE Impact
http://www.coresecurity.com/content/impact-v12-3
With the release of version 12.3, CORE Impact® Pro is the only solution to extend automated penetration testing to endpoints – allowing commercial and government organizations to proactively test desktop images at the OS and application levels without the need to challenge or exploit individual users with social engineering techniques. CORE Impact Pro’s new endpoint testing capabilities are completely revolutionary and are not offered by any other vulnerability assessment or penetration testing platform.
Pwn Plug Software Release 1.1 Now Available
http://www.pwnieexpress.com/downloads.html
Over on the Pwnie Express blog, Dave Porcello has announced the release of Pwn Plug System Software 1.1, a massive update to the companies Pwn Plug product.
This update addresses many of the issues with the existing software, such as the outdated release of Ubuntu it was based on and the lack of latest security tools. It also adds some very unique new features like the ability to wardial via GSM modem and control the Pwn Plug device with nothing more than SMS messages from any cell phone.
Orion Browser Dumper v1.0 released
http://www.darkcomet-rat.com/misctools.dc
This software is an advanced local browser history extractor (dumper), in less than few seconds (like for Browser Forensic Tool) it will extract the whole history content of most web browsers, such asInternet Explorer, Mozilla FireFox, Google Chrome, COMODO Dragon, Rockmelt and Opera.
SSLsplit 0.4.4
http://packetstormsecurity.org/files/112648/SSLsplit-0.4.4.html
SSLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. Connections are transparently intercepted through a network address translation engine and redirected to SSLsplit. SSLsplit terminates SSL/TLS and initiates a new SSL/TLS connection to the original destination address, while logging all data transmitted. SSLsplit is intended to be useful for network forensics and penetration testing.
New Version Of CORE Impact
http://www.coresecurity.com/content/impact-v12-3
With the release of version 12.3, CORE Impact® Pro is the only solution to extend automated penetration testing to endpoints – allowing commercial and government organizations to proactively test desktop images at the OS and application levels without the need to challenge or exploit individual users with social engineering techniques. CORE Impact Pro’s new endpoint testing capabilities are completely revolutionary and are not offered by any other vulnerability assessment or penetration testing platform.
Pwn Plug Software Release 1.1 Now Available
http://www.pwnieexpress.com/downloads.html
Over on the Pwnie Express blog, Dave Porcello has announced the release of Pwn Plug System Software 1.1, a massive update to the companies Pwn Plug product.
This update addresses many of the issues with the existing software, such as the outdated release of Ubuntu it was based on and the lack of latest security tools. It also adds some very unique new features like the ability to wardial via GSM modem and control the Pwn Plug device with nothing more than SMS messages from any cell phone.
Orion Browser Dumper v1.0 released
http://www.darkcomet-rat.com/misctools.dc
This software is an advanced local browser history extractor (dumper), in less than few seconds (like for Browser Forensic Tool) it will extract the whole history content of most web browsers, such asInternet Explorer, Mozilla FireFox, Google Chrome, COMODO Dragon, Rockmelt and Opera.
SSLsplit 0.4.4
http://packetstormsecurity.org/files/112648/SSLsplit-0.4.4.html
SSLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. Connections are transparently intercepted through a network address translation engine and redirected to SSLsplit. SSLsplit terminates SSL/TLS and initiates a new SSL/TLS connection to the original destination address, while logging all data transmitted. SSLsplit is intended to be useful for network forensics and penetration testing.
Saturday 12 May 2012
Information Security – Strategic and Tactical
As part of my series of blogs on the CISSP, CISA & CISM
certifications I am taking a look at how these fit into the Information
Security professional’s world. A successful Information Security Management Systems is
about having a clear vision and mission objectives (Strategic) and creating
effective and efficient action plans to put the vision and mission objectives
into action (Tactical).
<><>
Strategic Planning
The strategic planning is about how to accomplish the long
term goals and objectives of the organisation over a period of 3-5 years
typically. It is a macro-oriented approach with emphasis on the big picture for
the organisation
Tactical Planning
The tactical planning is about how to implement the policies
and decisions from the strategic planning on a micro-oriented approach over a
short time frame of 6 to 18 months.
ISMS Planning
For an ISMS to be successful, it must be aligned with the
business goals, the strategic planning enables the ISMS to be developed taking
into the high level mission statements of the organisation along with its long
term business plans. The tactical
planning will break each strategic goal into a series of incremental objectives
with a delivery date in the short to medium term with resourcing, budgets and
personnel critical components at the tactical plan level. Operational planning
is the short term task of implementing the tactical plans on a day to day
basis.
Information Security Certifications
CISM
The CISM is a premium certification for the Information Security
Manager and concentrates on the process of ensuring business goals are
incorporated into an ISMS, its domains are essential for the strategic planning
of a ISMS.
CISSP
The CISSP certification is a premium certification for the
Information Security professional and the (ISC)2 common body of
knowledge of the CISSP is essential for the tactical planning of an ISMS.
CISA
The CISA certification is the premium certification for ISMS
auditors and those who interact with auditors. The ISMS audit process ensures
the implementation and operation of the ISMS meets complies with the standards,
policies and controls the organisation have set themselves.
|
ISMS Area
| <><>
Certifications
| <><>
|
Compliance
| <><>
·
CISA
·
ISO 27001 Auditor/Lead Auditor
·
ISMS Auditor
·
GIAC Certifications
| <><>
|
Strategic
| <><>
·
CISM
·
GIAC Certifications
| <><>
|
Tactical
| <><>
·
CISSP
·
ISEB
·
GIAC Certifications
| <><>
|
Operational
| <><>
·
Non Vendor Certifications
·
Vendor certifications
| <><>
Monday 7 May 2012
Tools (7th May)
Weekly round up of pen test and forensic tools that have come to my attention over the last week, it is
not a comprehensive tool list but tools that I found interesting or details of
tools I use that have been upgrade.
maxisploit v1.0 released
http://maxisploit-scanner.googlecode.com/files/MaxISploit.rar
Scanner for SQL injection(error/blind) and XSS.Admin finder and shared hosting scanner (uses sameip.org service).
This tool has four purposes :
1. SQL injection :
a) Error based: it scans for vulnerable websites based on common SQL errors for variety of databases.
b) Difference (true/false) scan: it scans for sites that do not display SQL errors but yet are vulnerable , the concept behind this scan is true / false query to the database which will give different answers which will then be scanned and in case of difference in length and content site will be considered vulnerable.
2.XSS scanner : it encrypts XSS vector and tries to scan result from web server , if XSS vector is found inside source than site is vulnerable. It only uses GET request to web server. NOTE: It will scan for XSS vector but it will not test if alert or any other event really happened.
3. Admin scanner : it scans for admin login locations , based on default list or any other that you have supplied.Response code 200 and 306 is considered success.
4. Shared hosting scanner : it send request to sameip.org and then parses html for pages
An interesting tool category is this proof of concept tool which will help in showing what is vulnerably after a successful exploit of a system.
Ransack Post Exploitation Tool
http://www.infiltrated.net/scripts/ransack.sh
Ransack Post Exploitation Tool v 0.1 - Ransack is a post exploitation tool to be used by penetration testers. It is more of a proof of concept and its purpose is to grab any information deemed relevant on a system, post root compromise. This information may include config files, ssh keys, ssl keys, or any other information deemed valuable.
CIntruder v0.2 Beta Released
http://sourceforge.net/projects/cintruder/files/
CIntruder (Captcha Intruder) is an automatic pentesting tool to bypass captchas, the first beta was released on April 13th, a further update has been released on May 1st. Tools to automatically bypass Captcha are usefully in either bypassing a captcha or showing how easy it can to bypass an implementation.
sqlcake v1.1 - Automatic SQL injection and database information gathering tool.
http://sourceforge.net/projects/sqlcake/files/latest/download?source=files
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing. sqlcake offers a few useful functions to gather database information easily by sql injection usage. sqlcake also allows you to bypass magic quotes, dump tables and columns and gives you the possibility to run an interactive MySQL shell. sqlcake supports union stacked queries for real fast processing and blind injections with logarithmic techniques for saving time.
Updated vulnerabilities check for 10 packages including MediaWiki and added 2 servers database
http://nstalker.co.uk/category/latest-updates/
N-Stalker is now delivering new updates for N-Stalker 2012 Edition, including: Static Database: Updated vulnerabilities check for the following package: Invision Power Board IndexU PHP Live MediaWiki Cacti XMB Crafty Syntax Live Help MODx SugarCRM PHPSysInfo Updated Abyss server database check Updated PHP 5.4.x server database check Important: these updates are ONLY available for commercial edition users
maxisploit v1.0 released
http://maxisploit-scanner.googlecode.com/files/MaxISploit.rar
Scanner for SQL injection(error/blind) and XSS.Admin finder and shared hosting scanner (uses sameip.org service).
This tool has four purposes :
1. SQL injection :
a) Error based: it scans for vulnerable websites based on common SQL errors for variety of databases.
b) Difference (true/false) scan: it scans for sites that do not display SQL errors but yet are vulnerable , the concept behind this scan is true / false query to the database which will give different answers which will then be scanned and in case of difference in length and content site will be considered vulnerable.
2.XSS scanner : it encrypts XSS vector and tries to scan result from web server , if XSS vector is found inside source than site is vulnerable. It only uses GET request to web server. NOTE: It will scan for XSS vector but it will not test if alert or any other event really happened.
3. Admin scanner : it scans for admin login locations , based on default list or any other that you have supplied.Response code 200 and 306 is considered success.
4. Shared hosting scanner : it send request to sameip.org and then parses html for pages
An interesting tool category is this proof of concept tool which will help in showing what is vulnerably after a successful exploit of a system.
Ransack Post Exploitation Tool
http://www.infiltrated.net/scripts/ransack.sh
Ransack Post Exploitation Tool v 0.1 - Ransack is a post exploitation tool to be used by penetration testers. It is more of a proof of concept and its purpose is to grab any information deemed relevant on a system, post root compromise. This information may include config files, ssh keys, ssl keys, or any other information deemed valuable.
CIntruder v0.2 Beta Released
http://sourceforge.net/projects/cintruder/files/
CIntruder (Captcha Intruder) is an automatic pentesting tool to bypass captchas, the first beta was released on April 13th, a further update has been released on May 1st. Tools to automatically bypass Captcha are usefully in either bypassing a captcha or showing how easy it can to bypass an implementation.
sqlcake v1.1 - Automatic SQL injection and database information gathering tool.
http://sourceforge.net/projects/sqlcake/files/latest/download?source=files
sqlcake is an automatic SQL injection exploitation kit written in Ruby. It's designed for system administration and penetration testing. sqlcake offers a few useful functions to gather database information easily by sql injection usage. sqlcake also allows you to bypass magic quotes, dump tables and columns and gives you the possibility to run an interactive MySQL shell. sqlcake supports union stacked queries for real fast processing and blind injections with logarithmic techniques for saving time.
Updated vulnerabilities check for 10 packages including MediaWiki and added 2 servers database
http://nstalker.co.uk/category/latest-updates/
N-Stalker is now delivering new updates for N-Stalker 2012 Edition, including: Static Database: Updated vulnerabilities check for the following package: Invision Power Board IndexU PHP Live MediaWiki Cacti XMB Crafty Syntax Live Help MODx SugarCRM PHPSysInfo Updated Abyss server database check Updated PHP 5.4.x server database check Important: these updates are ONLY available for commercial edition users
Sunday 6 May 2012
CISSP, CISA & CISM
I am current this month working on deliverying CISSP and CISA training as well as doing the CISM exam and I thought as I go through the month I will talk about the courses and how I feel they compare and relate to the Information Security Professional
Top security certifications
Some of the top Information security certifications are offered by International Information Systems Security Certification Consortium (ISC)2 and ISACA (previously was known as Information Systems Audit and Control Association, but now just uses the acronym).
There is a very excellent sent of certifications offered by Global Information Assurance Certification (GIAC) which whilst not described here I will be hoping to discuss in future, I currently don't have first hand experience of GIAC and the certifications offered.
Summary of the certifications
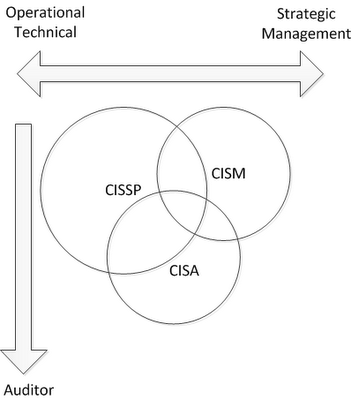
The certifications themselves although overlap on some content have different focuses, the most obvious is the CISA and its focus on auditing, this is a good certification not only for auditors but for those who deal with auditors.
The Venn diagram shows how the certifications complement each other with different focuses on auditing, or strategic, or tactical functions.
ISACA say that earning the CISSP and/or the CISA credential is complementary to the attainment of the CISM credential and is encouraged.
Accreditation
CISSP, CISA & CISM are accredited to ANSI ISO/IEC Standard 17024:2003, is an International Standard which sets out criteria for an organization's certification program for individual persons.
The issues that ISO 17024 tackles can be summarized as:
Where competency is typically described as:
“The demonstrated ability to apply knowledge, skills and attributes”
The factor that all these certifications have been accredited show the effort the organisations put in to maintating the certifications with the standard and that they believe they are important certifications for a professional to hold
Certification Content
Each of the certifications divide the content in to domains of knowledge, the current domain structure of the certifications is shown below. I will be looking at the certifications and the content of the domains in more detail later this month.
Top security certifications
Some of the top Information security certifications are offered by International Information Systems Security Certification Consortium (ISC)2 and ISACA (previously was known as Information Systems Audit and Control Association, but now just uses the acronym).
There is a very excellent sent of certifications offered by Global Information Assurance Certification (GIAC) which whilst not described here I will be hoping to discuss in future, I currently don't have first hand experience of GIAC and the certifications offered.
Summary of the certifications
Certification
|
Summary
|
Body
|
CISSP
|
The qualification of Certified Information Systems Security
Professional (CISSP) was
created in 1989. It is the one of the most popular and well known security
certification. The CISSP study
programme gives a broad overview of information security. Certification is by
way of a multiple choice examination that covers 10 subject areas, including
'Cryptology', 'Law, Investigation and Ethics'.
|
(ISC)2
|
CISM
|
The Certified Information Security Manager (CISM) programme is
intended to recognise those with the technical and managerial abilities to
oversee an enterprise wide information security system. Individuals in such a
role require an understanding of business goals and IT strategies, as well as
the ability to define sensible security policies, acceptable usage policies
for the use of email and Internet, and the configuration of the organisations
firewall.
The CISM certification is for the individual, who manages, designs,
oversees and/or assesses an enterprise’s information security (IS). The CISM
certification promotes international practices and provides executive
management with assurance that those earning the designation have the
required experience and knowledge to provide effective security management
and consulting services.
|
ISACA
|
CISA
|
The Certified Information Systems Auditor (CISA) is recognised as the
standard of achievement for those who audit, control, monitor and assess an
organization’s information technology and business systems.
With a growing demand for professionals possessing IS audit, and
control skills, CISA has become a preferred certification program by
individuals and organizations around the world. CISA certification signifies
commitment to serving an organisation and the IS audit, control industry
|
ISACA
|
The certifications themselves although overlap on some content have different focuses, the most obvious is the CISA and its focus on auditing, this is a good certification not only for auditors but for those who deal with auditors.
The Venn diagram shows how the certifications complement each other with different focuses on auditing, or strategic, or tactical functions.
ISACA say that earning the CISSP and/or the CISA credential is complementary to the attainment of the CISM credential and is encouraged.
- Defining what it is you examine (the competencies)
- Knowledge, skills and personal attributes
- Examination must be independent
- Examination must be a valid test of competence
CISA domains (2011)
Domain 1
|
The Process of Auditing Information Systems
|
Domain 2
|
Governance and Management of IT
|
Domain 3
|
Information Systems Acquisition, Development and Implementation
|
Domain 4
|
Information Systems Operations, Maintenance and Support
|
Domain 5
|
Protection of Information Assets
|
CISM domains (2011)
Domain 1
|
Information Security Governance
|
Domain 2
|
Information Risk Management and Compliance
|
Domain 3
|
Information Security Program Development and Management
|
Domain 4
|
Information Security Incident Management
|
CISSP Domains (2012
Candidate Information Bulletin)
Domain 1
|
Access Control
|
Domain 2
|
Telecommunications and Network Security
|
Domain 3
|
Information Security Governance and Risk Management
|
Domain 4
|
Software Development Security
|
Domain 5
|
Cryptography
|
Domain 6
|
Security Architecture and Design
|
Domain 7
|
Operations Security
|
Domain 8
|
Business Continuity and Disaster Recovery Planning
|
Domain 9
|
Legal regulations, investigations, and compliance
|
Domain 10
|
Physical and Environmental Security
|
Exam comparison
Exam
|
Length
|
No of Questions
|
Pass score (Scaled)
|
Max score (scaled)
|
Frequency
|
CISA
|
4
|
200
|
450
|
800
|
twice a year
|
CISM
|
4
|
200
|
440
|
800
|
twice a year
|
CISSP
|
6
|
250 *
|
700
|
1000
|
Frequently
|
*25 questions are experimental and not graded
Saturday 5 May 2012
April Port Scans
Analysis of the logs files from my ADSL router for April, there was a large peak of UDP scans which was traced to Akamai who where attempted to connect to the peer to peer network component of their download engine that Adobe use. This peer to peer connection is used by Akamai to allow copies of the download products to be retrieved from the 'client' machines spreading the load from their servers to those who download the producta. The download engine sends messages to the Akamai servers as to which UDP ports it is listening on, however although it may open the ports in the host firewall, the connections where rejected by the firewall in my ADSL router.
|
Month
|
No Attacks
|
DOS
|
Port Scans
|
Unique IP
|
Unique Countries
|
|
Apr 2012
|
234
|
234
|
0
|
54
|
5
|
|
Country
|
IP Sources
|
Attacks
|
|
Turkey
|
25
|
25
|
|
China
|
13
|
66
|
|
USA
|
9
|
97
|
|
France
|
3
|
18
|
|
Japan
|
2
|
10
|
|
UK
|
2
|
11
|
Subscribe to:
Posts (Atom)